Implementing Wireless Intrusion Detection System
Posted in Networking, Security with tags muhrizky, wids on September 28, 2014 by muhrizkyNTP on Linux
Posted in Networking, Security with tags muhrizky, ntp on September 28, 2014 by muhrizkyA couple of months ago I have some task to create an environment of all network devices in order to be synchronize with differentiation of maximum 2 seconds. Which is impossible to set manually beside of using a Network Time Protocol (NTP) synchronization. This protocol works on Stratum number hierarchy where the lowest number should be the most reliable. NTP need TCP port 123 in order to communicate, do a further check on an exclusion inside the iptables script.
For those who wants a straight-forward setup, NTP can also run on Windows environment which is out-of-scope discussion within this blog. It was easy task anyway by using a left click of a mouse within a Windows interface.
Packages that we need to get from the repository are ntp and ntpdate.
Within Debian derivative run the command #apt-get install ntp ntpdate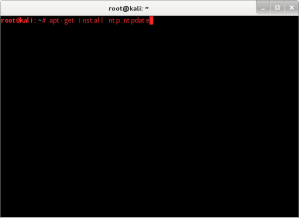
In Slackware there is no automation for each installation, so that we exactly need to know those packages dependencies.
Next step is the most interesting computing experience for anyone who loves Linux environment, which is script editing in order to configure the synchronizing server. The script was located on /etc/ntp.conf then find a line that starts with:
# pool.ntp.org maps to about 1000 low-stratum NTP servers. # Your server will pick a different set every time # it starts up. Please consider joining the # pool http://www.pool.ntp.org/join.html server 0.id.pool.ntp.org iburst server 1.id.pool.ntp.org iburst server 2.id.pool.ntp.org iburst server 3.id.pool.ntp.org iburst
The security part was to restrict synchronization locally for a loopback adapter and for the primary host do a broadcasting.
# Local users may interrogate the ntp # server more closely. restrict 127.0.0.1 restrict ::1 # If you want to provide time to your # local subnet, change the next line. # (Again, the address is an example only.) broadcast 172.16.7.3
Restart the service where currently this is pre-configured as an Init script, including for the setup of IP config (static IP, gateway, DNS) by run command #service ntp restart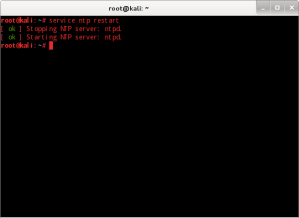
The last one is to monitor the synchronization between the public Stratum which is only possible to be done after all the configuration script and command was good. Run the command #ntpq -p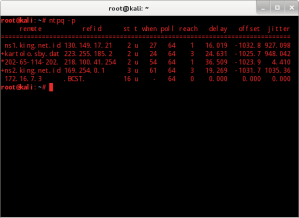
The local Clients synchronization can be determine by run command #ntpdc -c monlist
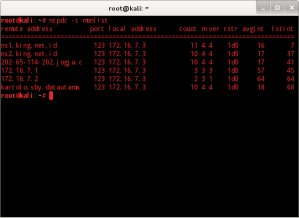
Update!!! This command was vulnerable of DoS attack as it was mention by this CVE-2013-5211
Below is the propose script modification to be applied and very recommended to create the egress filtering on each data packet flow on your firewall in order to prevent any further DoS attack inside of the network.
# By default, exchange time with everybody, but don't allow configuration. restrict default kod notrap nomodify nopeer noquery restrict -6 default kod notrap nomodify nopeer noquery # Local users may interrogate the ntp server more closely. restrict 127.0.0.1 restrict ::1 # Clients from this (example!) subnet have unlimited access, but only if # cryptographically authenticated. restrict 172.16.7.0 mask 255.255.255.224 notrust

